2.16
Workflow Editor
New Simulator
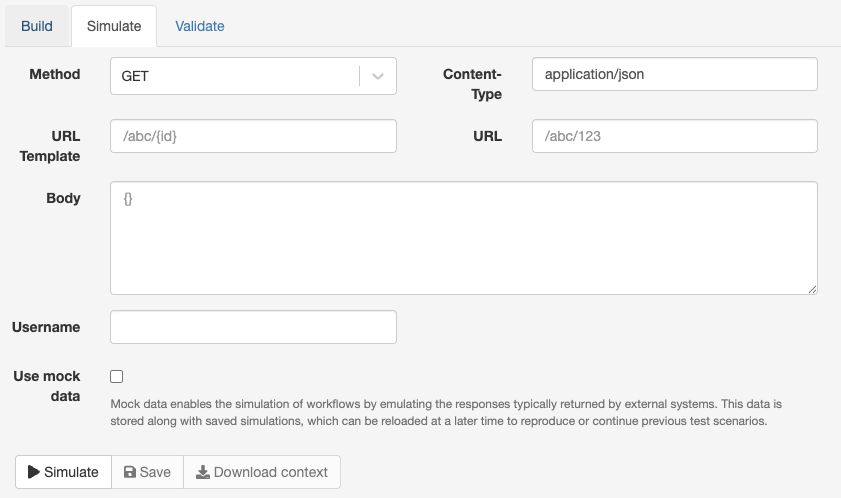
A new simulator has been introduced to enable simulation of incoming HTTP requests by specifying the target URL, headers, and request body as they would be received by the Core. When a simulation is executed, the Core processes the workflow in-memory and generates a visual diagram showing the nodes traversed during execution. Additionally, the full context data can be downloaded for inspection.
For nodes that interact with external systems (such as query nodes), mock data can be provided in JSON format. Instead of reaching out to the actual external systems, the simulator uses this mock data to emulate the expected responses.
Simulations can be saved to the database and later reloaded or directly replayed.
Enhanced Asynchronous Workflow Support
Two new nodes, "Wait Callback" and "Resume Execution", have been introduced to enhance support for asynchronous workflows. These nodes allow you to define a custom identifier to pause execution and later resume it when an HTTP request with the matching ID is received by APIO Core. This provides a more flexible and robust alternative to the previous asynchronous JSON call mechanism, which relied on less adaptable request and response values.
Workflow Version Reinstantiation
A new button has been added to the workflow editor, allowing users to re-instantiate a previously committed version of a workflow as the current working version.

Identity and Access Management
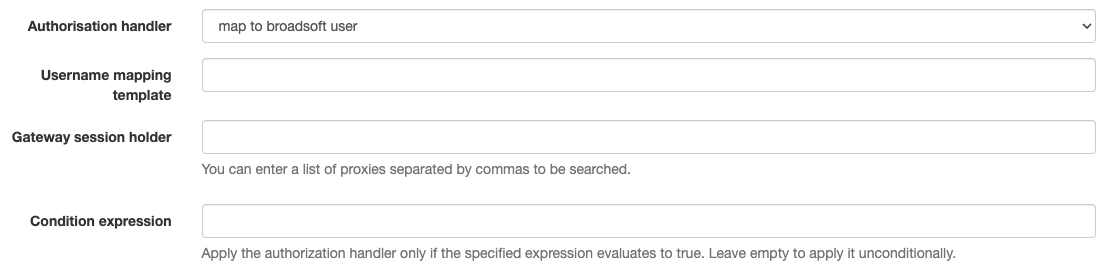
Conditional Authorization Handlers
It is now possible to define a condition when configuring an authorization handler within an SSO configuration. This condition is evaluated during the authentication process, and the handler is applied only if the condition returns true. This enables advanced scenarios—for example, validating certain users from an external IdP against the Broadworks platform, while allowing others to be authenticated solely as local users.
User Management Enhancements
The user management page has been improved to indicate whether a user is local or backed by an external IdP. Additionally, deleting a user now triggers a confirmation alert.
Integration
Gateway Bearer Authentication
The Bearer authentication method has been added to the list of available options when configuring gateways, providing support for token-based access control in HTTP requests.

Operations
Improved Context Variables Display
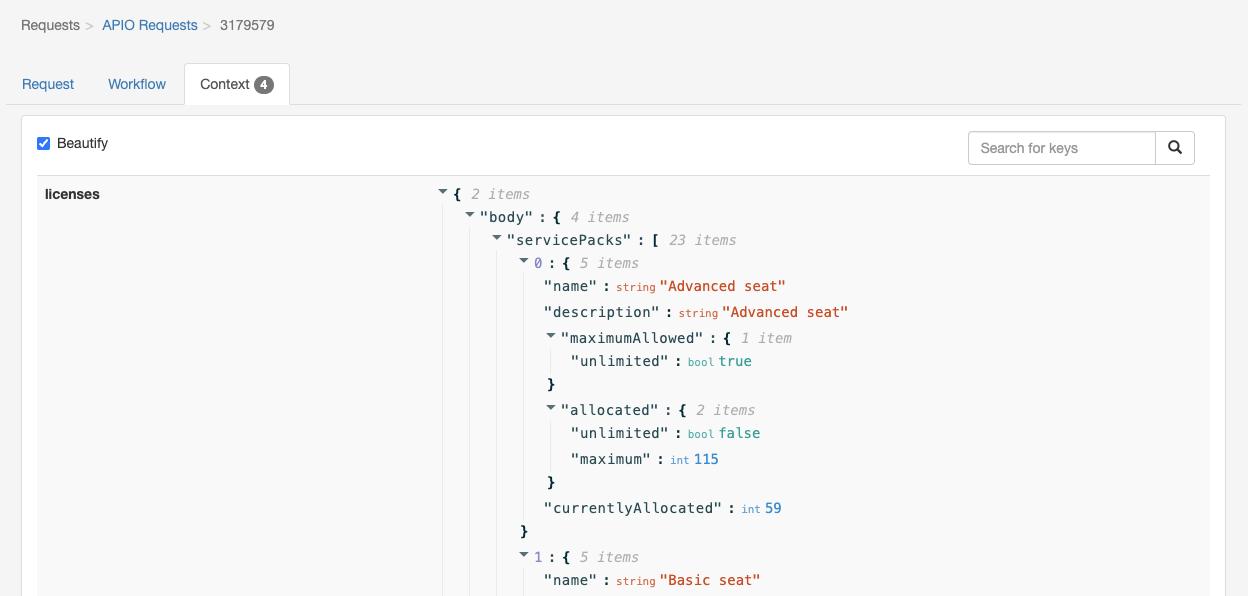
In the transaction details, the display of context variables has been enhanced with automatic JSON beautification for improved readability. When context values contain embedded JSON, the tool attempts to parse and format it as well, making nested data structures easier to interpret.
Improved Request Export Capabilities
The requests export tool has been enhanced to include additional columns in the CSV output file, such as the workflow name, a link to the workflow, the HTTP method, and the URL.
Example
id;workflow;workflow_name;workflow_url;method;url;err_workflow;request_id;tenant;site;numbers;status;instance_status;owner;created_on
3172019;315;f4b_get_tenant_and_group_licenses;/transactions/config/activities/editor/315;get;/api/v01/p1/tenants/UAT_Zeratul_ent1/licenses/;;7222752;UAT_Zeratul_ent1;;;SUCCESS;CLOSED_IN_SUCCESS;rben;2025-06-10 12:06:36.024203 +0000 UTCNew Prometheus Metrics
The /metrics endpoint (accessible on port 9090 by default if license is enabled) has been enhanced to expose additional performance metrics. These include, among others, session holder latency and the number of active requests per session holder, providing greater visibility into system behavior and performance.
Database Replication Alarm
A new database replication alarm has been introduced to detect issues in the replication stream. It triggers when replication from the master database to the standby database is interrupted, enabling faster detection and resolution of potential data redundancy problems.
Security
API Tokens Display
API tokens generated for users are now displayed only once at the time of creation. Afterward, the tokens are hidden to enhance security and prevent unauthorized access.
Patch Versions Release Notes
Release 2.16.0
| Pull id | Fix |
|---|---|
| 470 | fixed Hawk authentication; improved CI/CD pipeline |
| 462 | added attempt at beautifying all context variables as JSON |
| 461 | fixed ProvUI typo |
| 459 | added bearer authentication to list of supported gateway authentication options |
| 456 | added support for mocking request user approval node; added error description in tooltip for node failures |
| 454 | fixed cell form layout |
| 453 | added simulator button to download context |
| 450 | fixed OIDC code verifier length |
| 446 | added option to beautify the request context on transactions detail page |
| 444 | added more specific retry conditions for HTTP call nodes |
| 442 | hidden token for entity users |
| 440 | improved Prometheus metrics with statistics for workflows, session holders & users |
| 438 | added in-GUI workflow simulator with the option to mock data |
| 435 | removed LABEL from docker images |
| 430 | fixed template renderer memory leak |
| 428 | fixed workflow editor note cell width auto-sizing |
| 427 | fixed hawk authentication: corrected hash and mac computation |
| 424 | fixed escaping handling for DB migration script when DB URL contains escaped characters |
| 423 | improved gateway status view when check option is disabled |
| 422 | removed integrated logs viewer |
| 421 | restricted access to activities API endpoint |
| 420 | opened template playground tool (removed license) |
| 419 | updated build process to read software version from latest GIT tag |
| 416 | added DB replication alarm |
| 415 | added index on instances.original_request_id to speed up scheduled jobs search |
| 408 | added an option to specify a condition for applying the authorization handler conditionally in SSO integrations |
| 400 | fixed oauth2 body handling when log level set to debug |
| 398 | added optional dumping of TLS session secrets for debugging purposes |
| 397 | added support for ui_id parameter while rendering 2FA by email template |
| 391 | fixed asynchronous-json-call help link |
| 389 | added button to re-instantiate existing workflow version as working version |
| 382 | added new nodes Wait callback and Resume execution to create and resume external callbacks using any callback id |
| 380 | fixed push to NAS, removed push to GDrive |
| 379 | switch to free version of go releaser |
| 377 | removed inline doc build, updated links |
| 376 | adapted password rules endpoint to use the active BWGW session if available to retrieve password rules from backend |
| 369 | added debug topics for oauth2 tokens |
| 365 | adapted Webex gateway to proxy requests starting with identity |
| 363 | fixed email sending to multiple recipients with SSL |
| 357 | improved requests export with workflow name/link, method, URL |
| 356 | improved node Synchronous response to allow specifying additional HTTP response headers and returning non-JSON body by setting the Content-Type header |
| 354 | fixed handling when nodes contain a dot in name |
| 350 | fixed passkey removal button |
| 348 | adapted top menu bar to be full width |
| 347 | aligned special characters supported for passwords on UCCH SCP |
| 346 | fixed home for user profile |
| 343 | fixed multiple recipients handling in email with SSL |
| 342 | added warning when deleting a remote user |
| 341 | added a backend column to the users list to indicate the IdP (Identity Provider). |
| 340 | added audit data recording for login operation |
| 337 | added svg and ico to allowed content types |
| 335 | migrated woodpecker pipeline |
| 333 | adapted option -rateLimit to allow disabling rate limiter |
| 327 | fixed account lockout duration handling |
| 326 | added debug topics logging framework |
| 325 | hidden token from user profile |
| 324 | added username display in top bar; fixed active tab styling |
| 323 | added application 2-level config to Provisioning UI |
| 322 | implemented different modes of operation (deny/allow/force password) when password is expired on Broadsoft IdP |
| 317 | YAOH UI as subtree |
Upgrade from 2.15
If prometheus metrics are used, you need to request and install new licence with metrics enabled. Otherwise this release does not require any special steps for the upgrade. Simply follow the generic update procedure outlined in the Deployment Guide.
Before upgrading check that in systems->settings->configuration page, in the raw tab, json configuration contains the following structure for alarms:
{"alarms": {"alarms":{
If this structure is not present contact R&D for a solution.
Downgrade to 2.15
This release does not require any special steps for the downgrade. Simply follow the generic update procedure outlined in the Deployment Guide.
